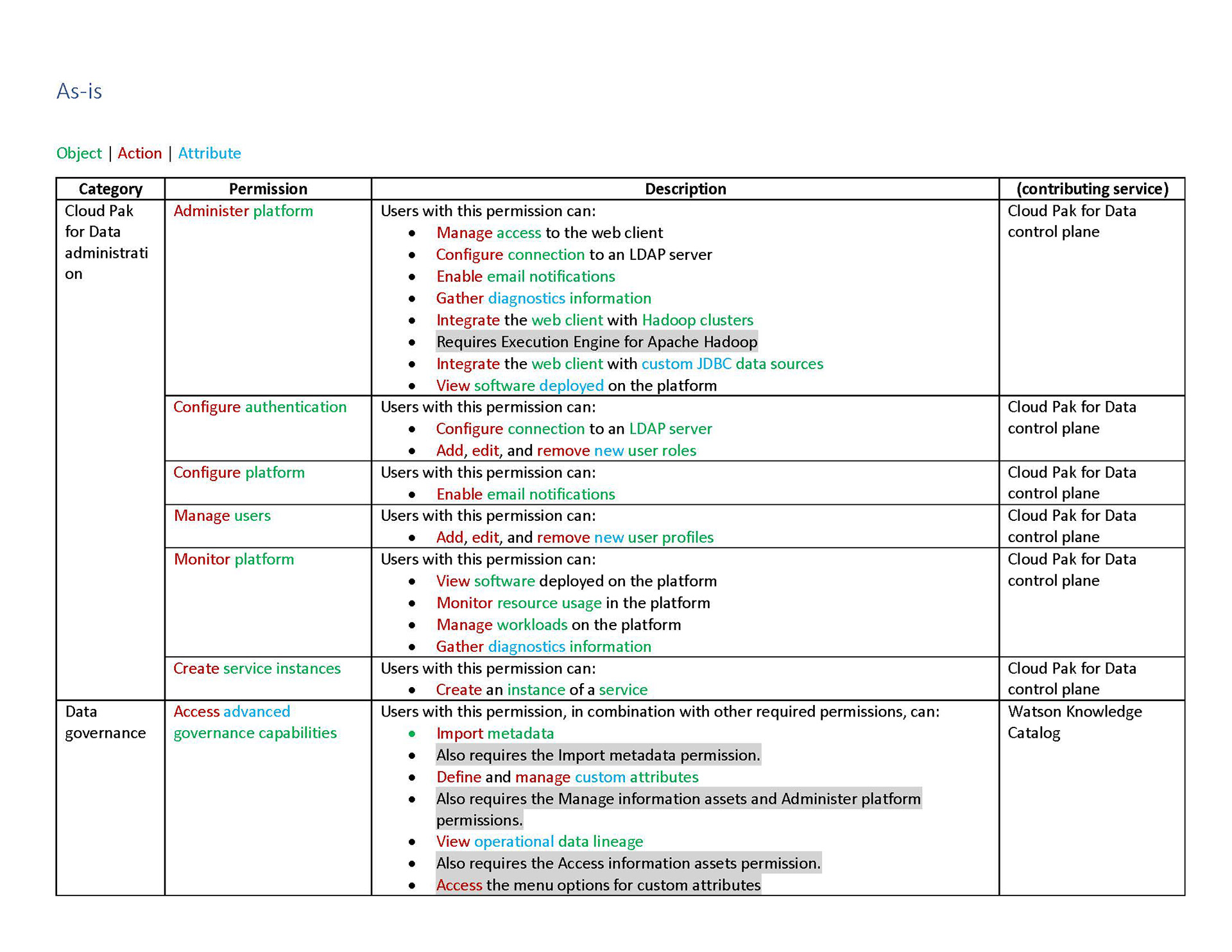
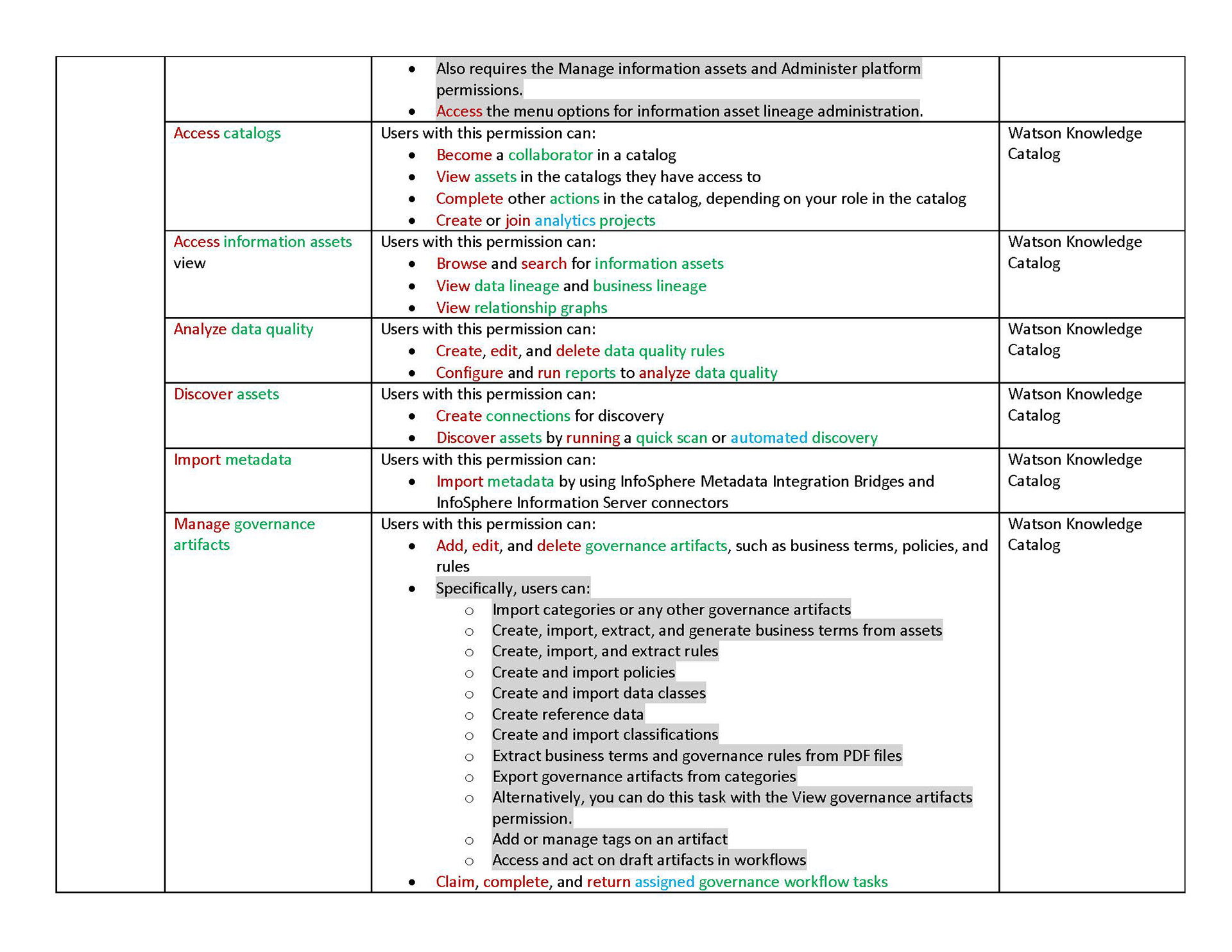
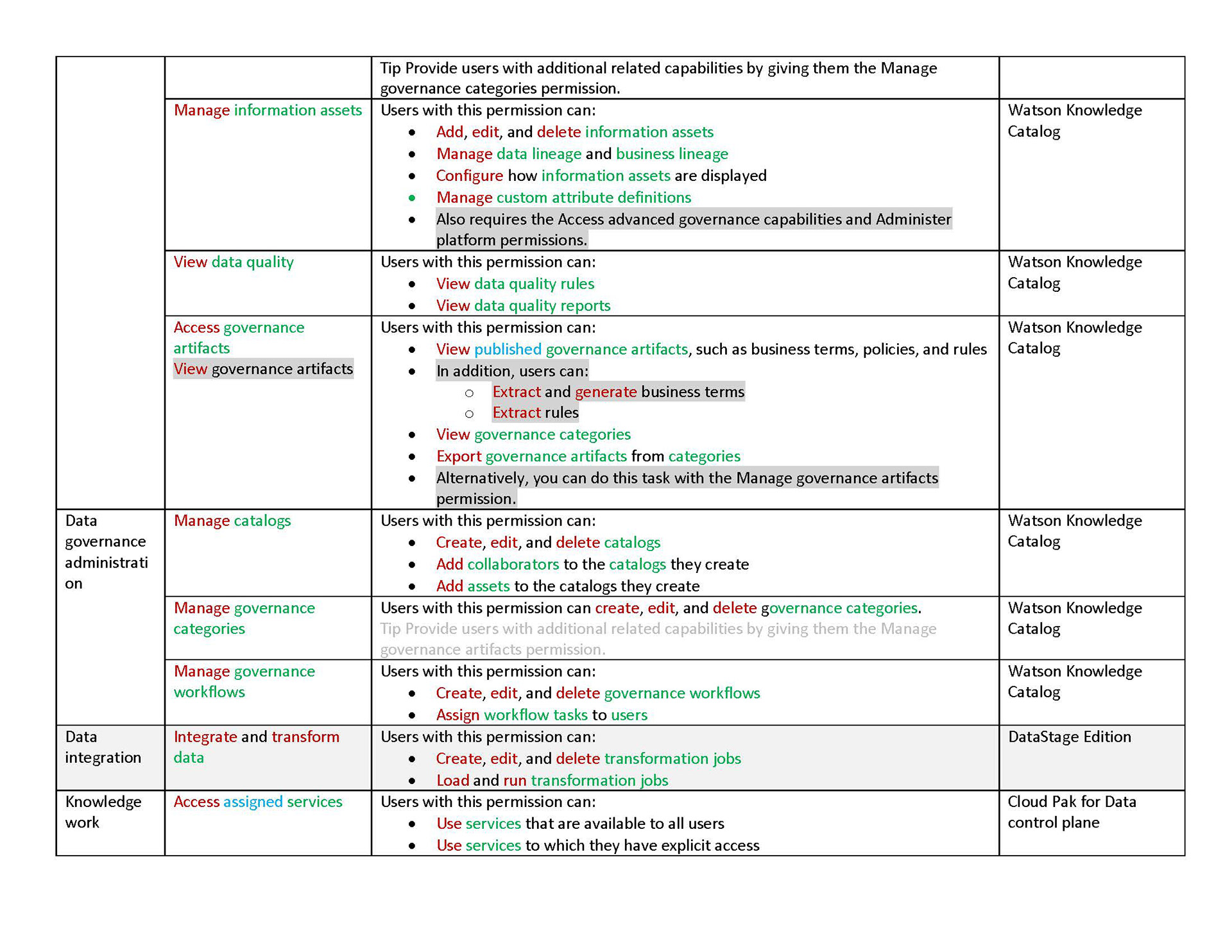
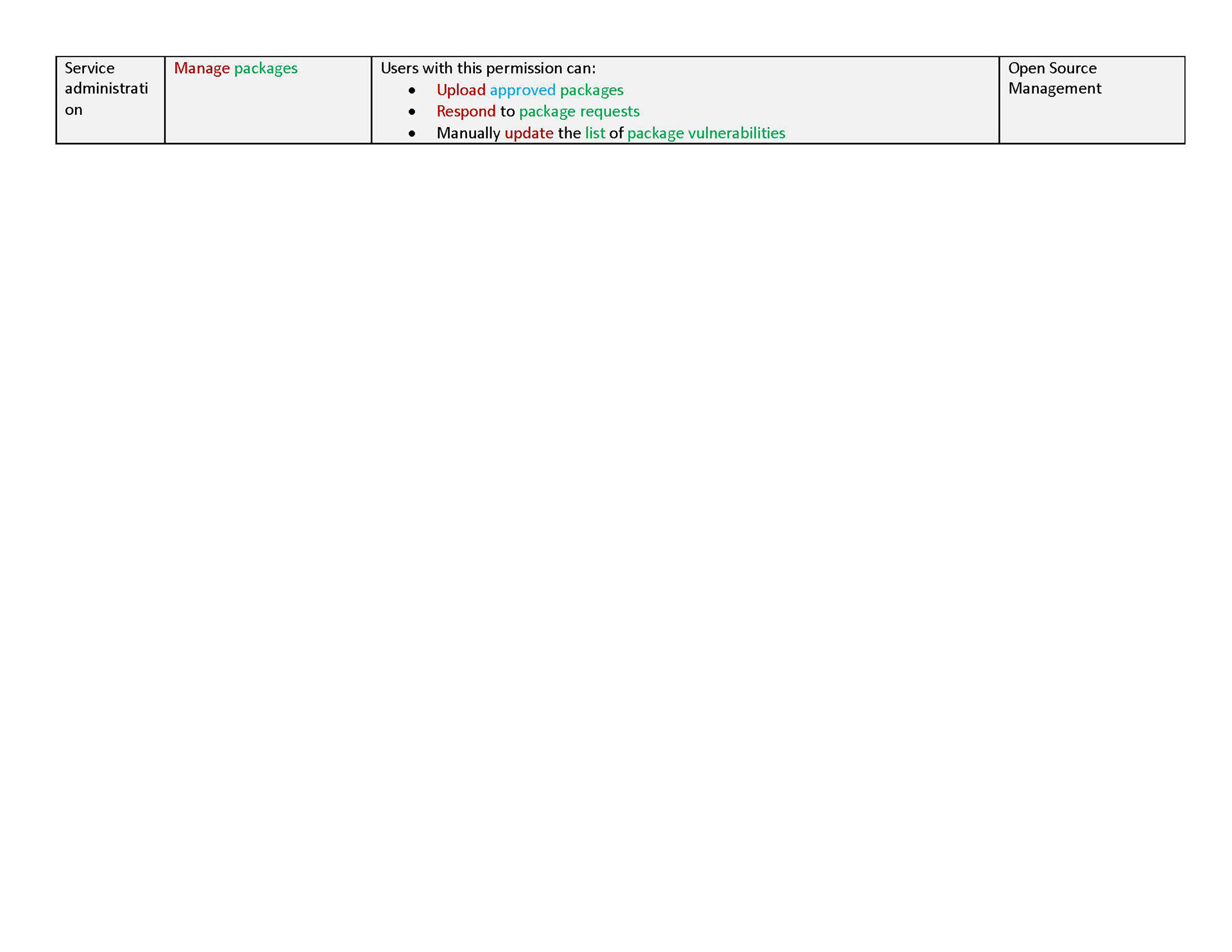
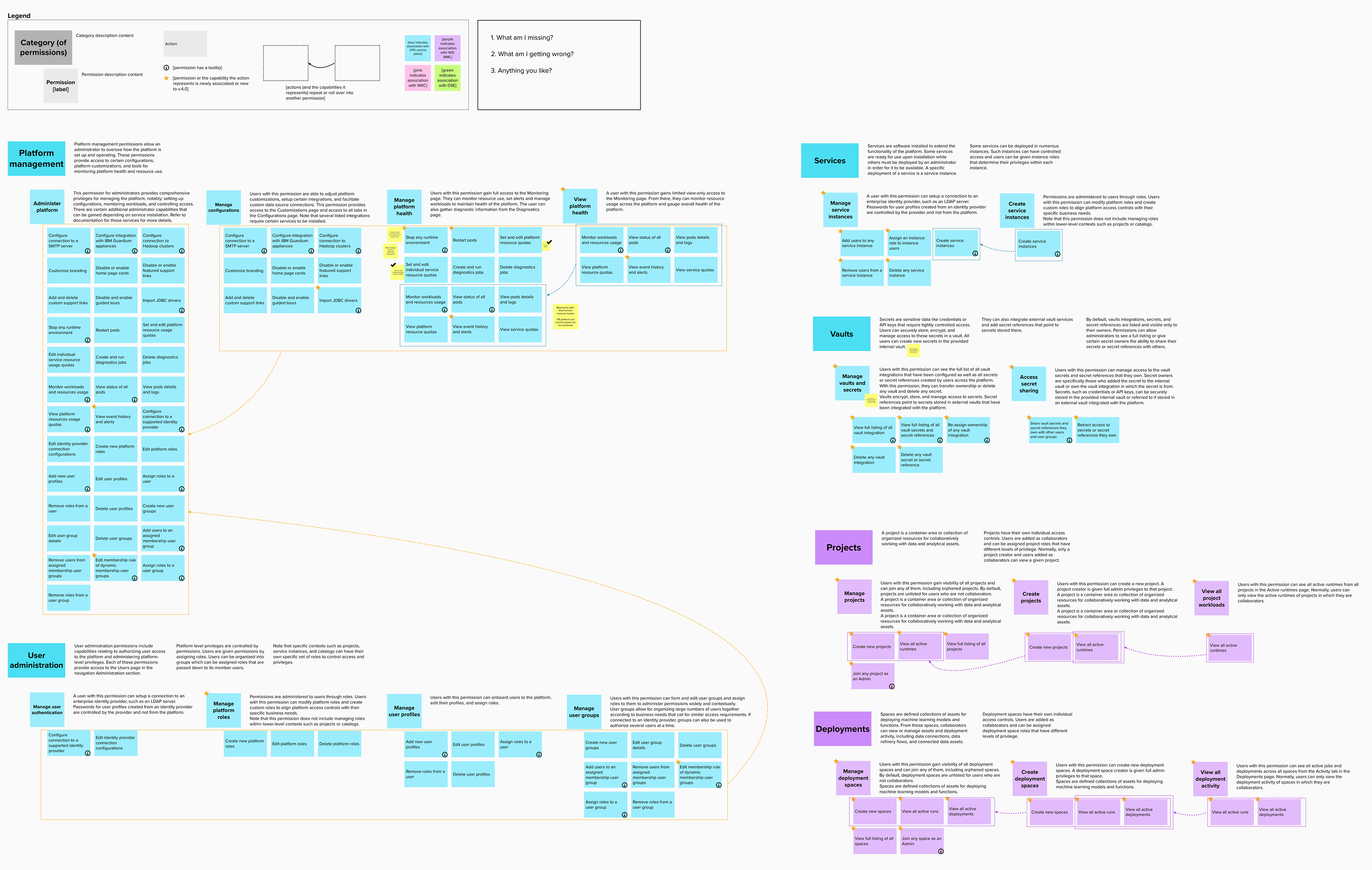
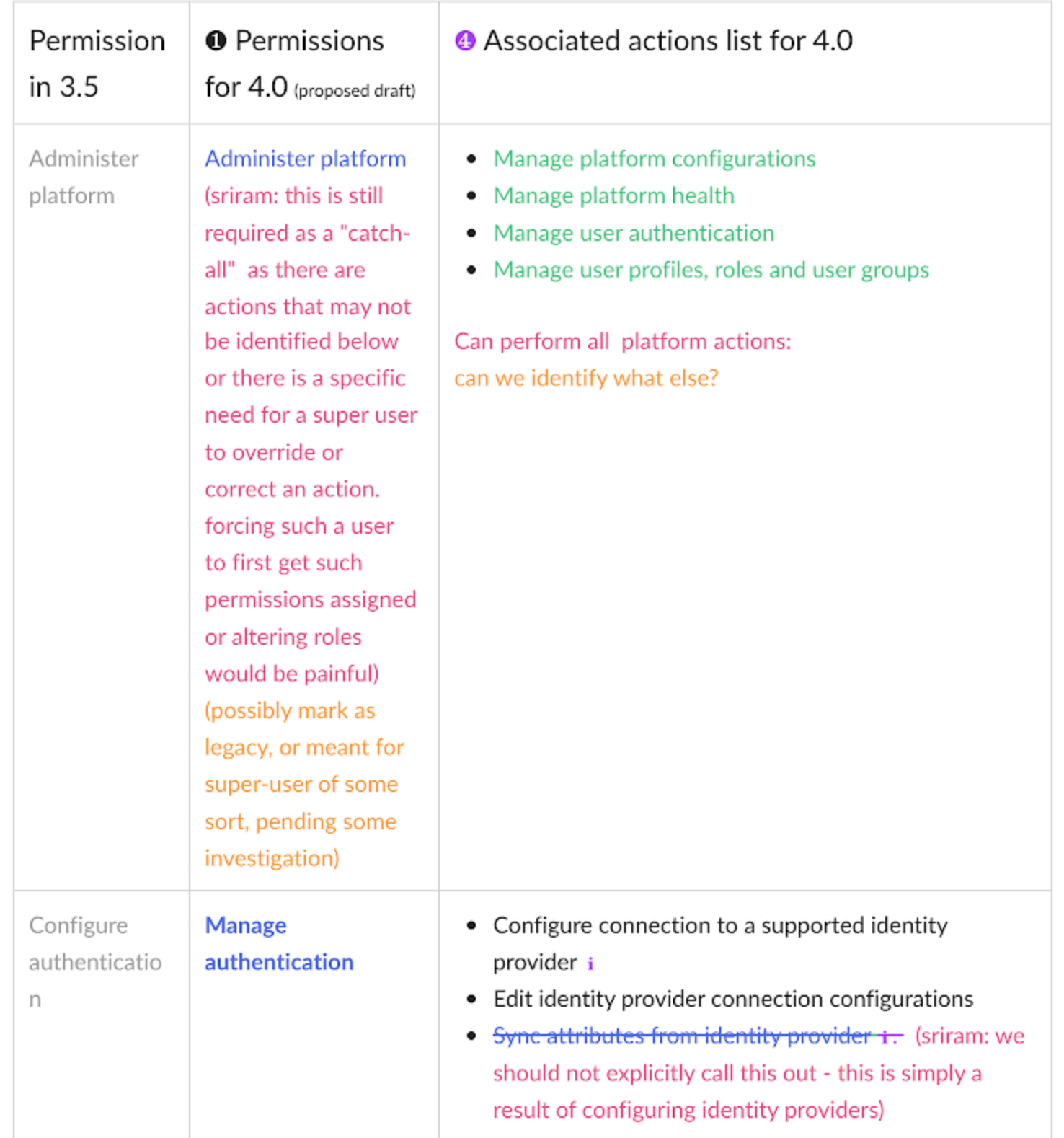
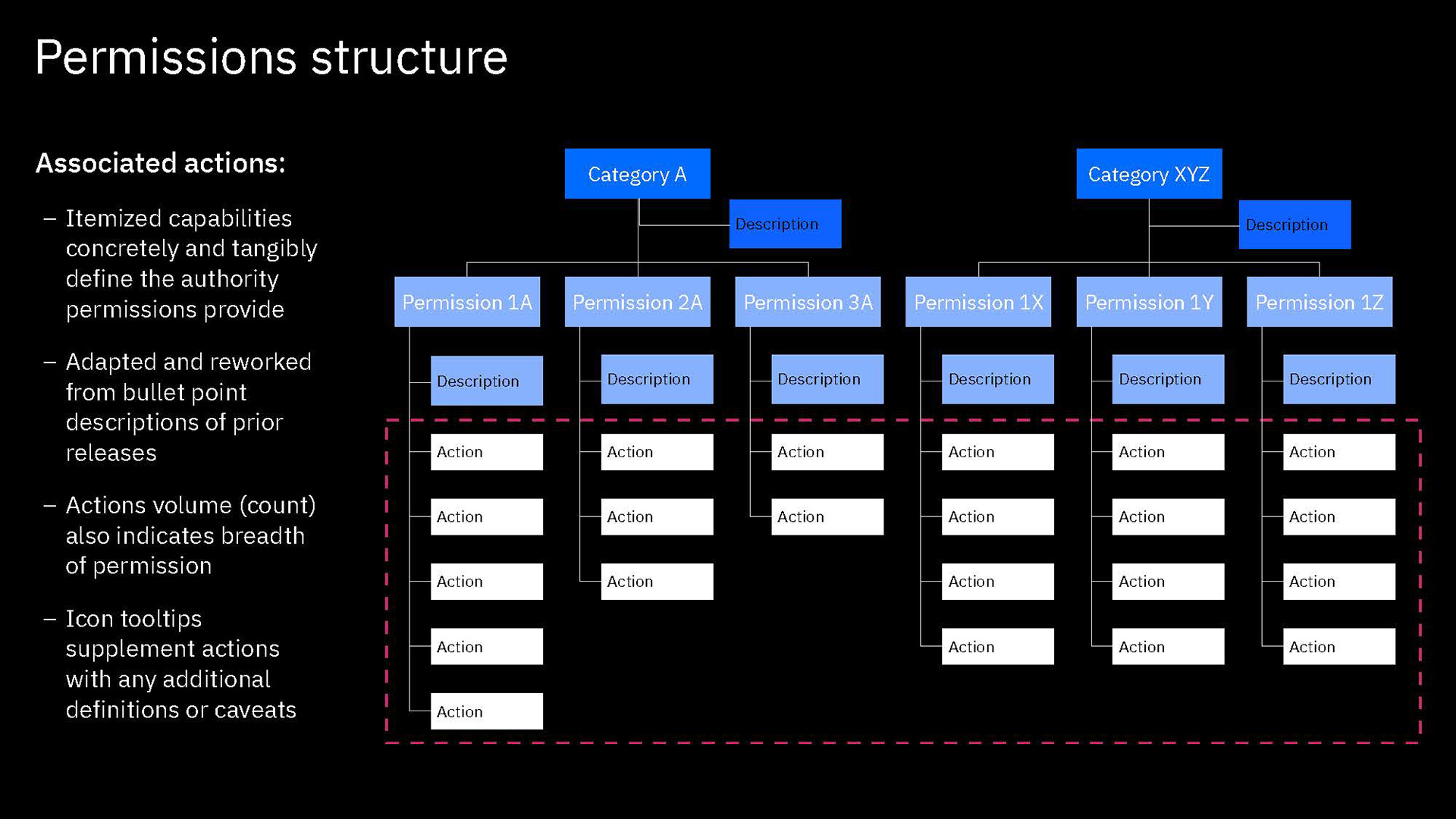
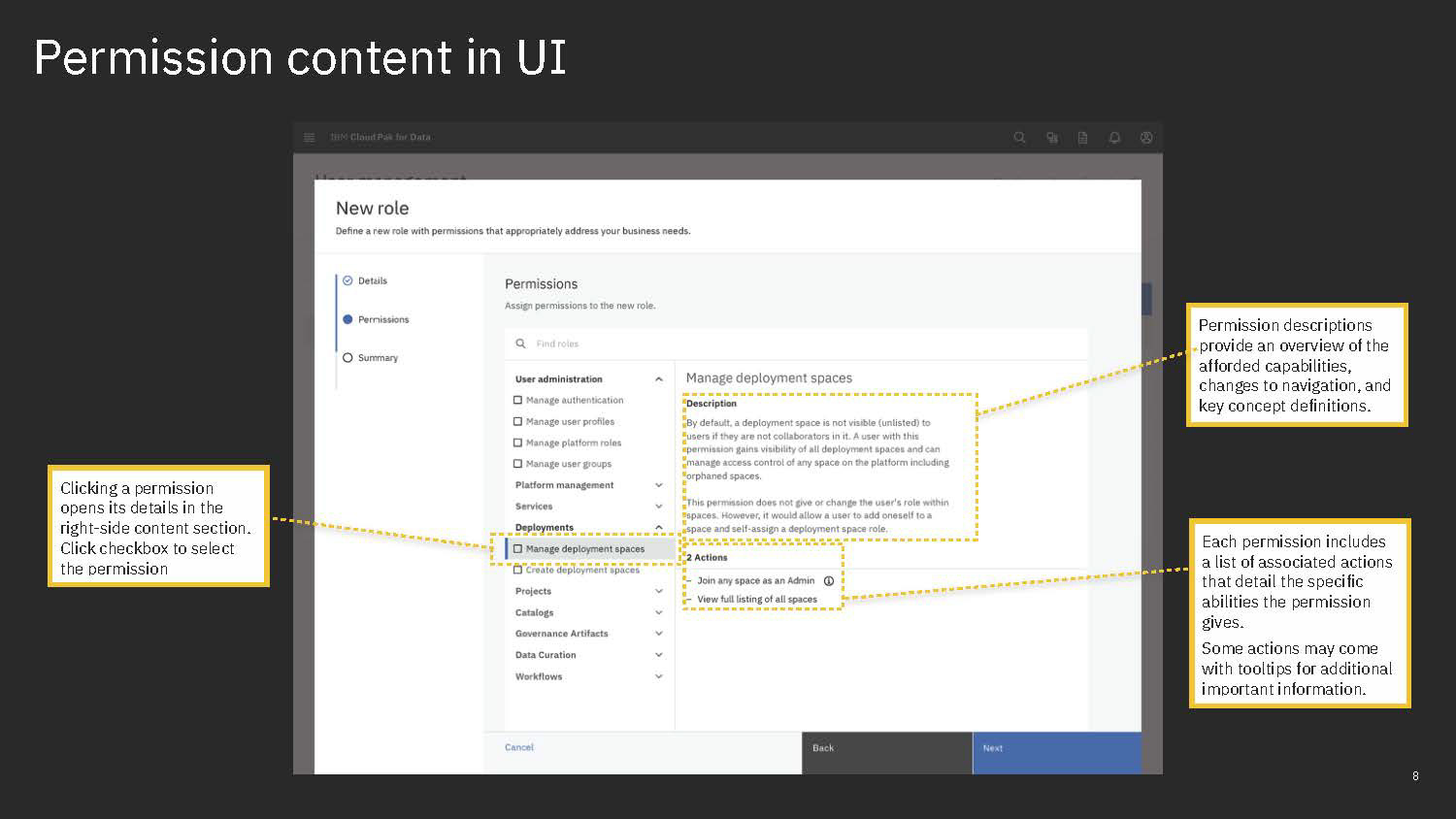
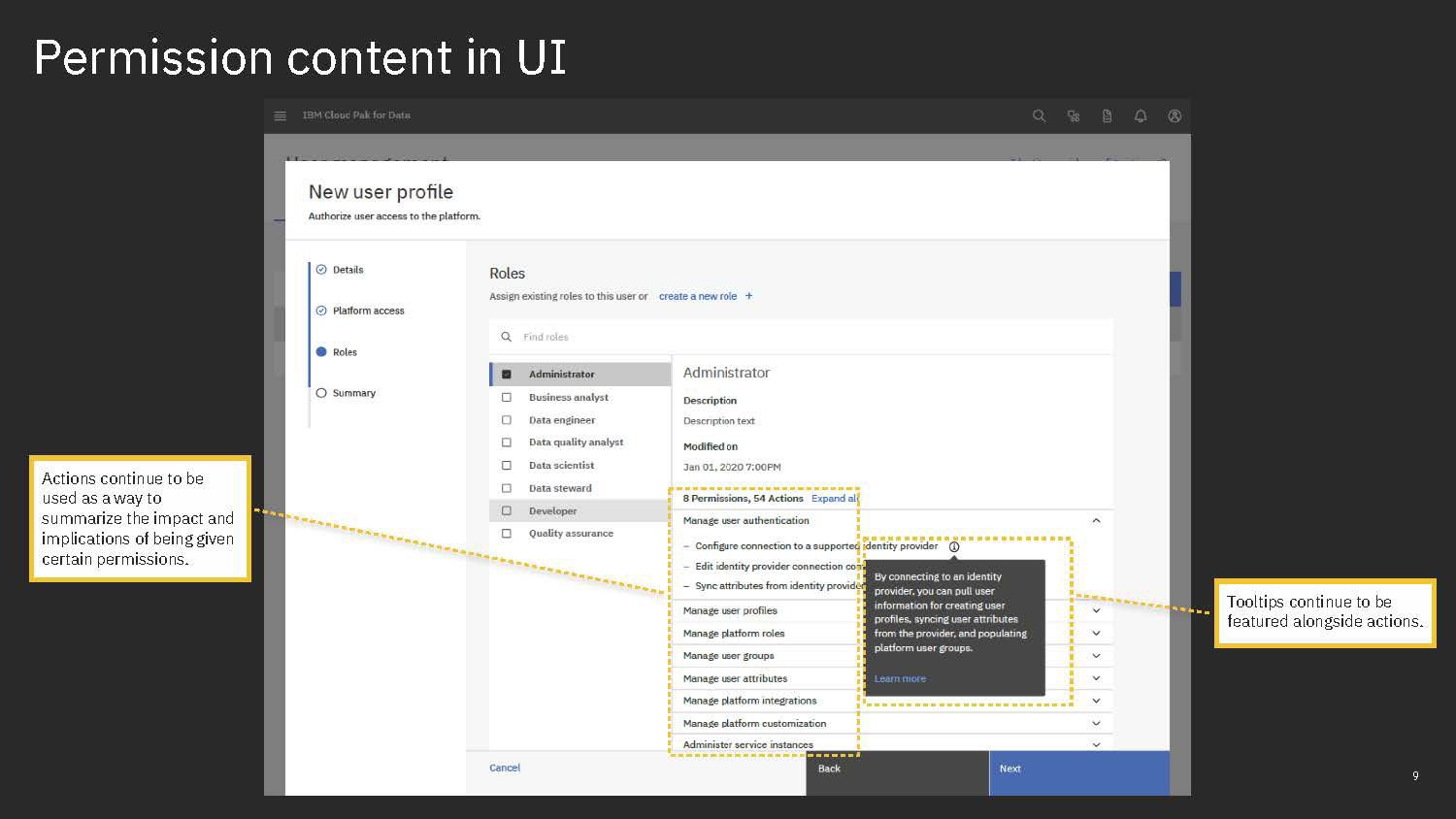
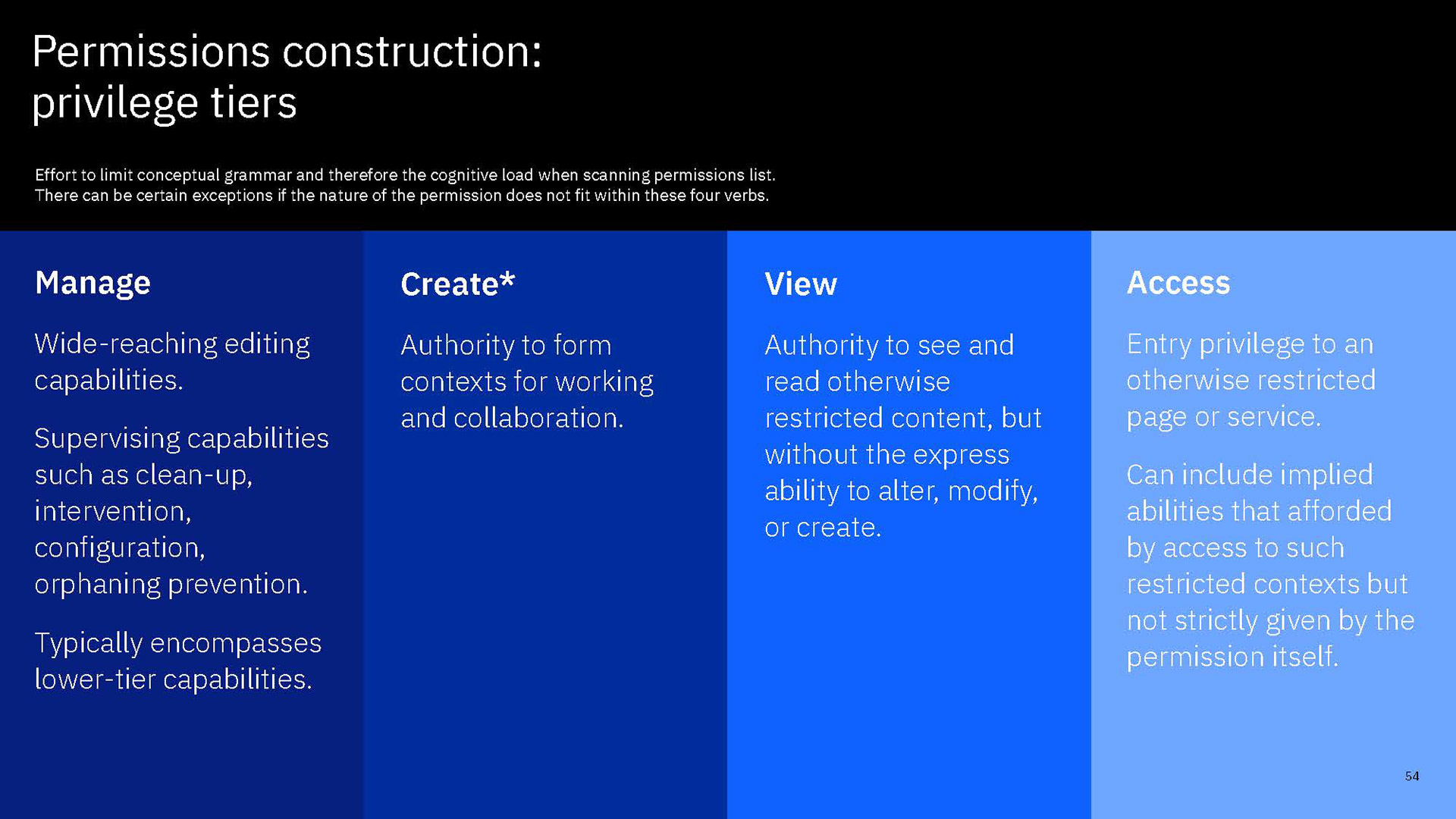
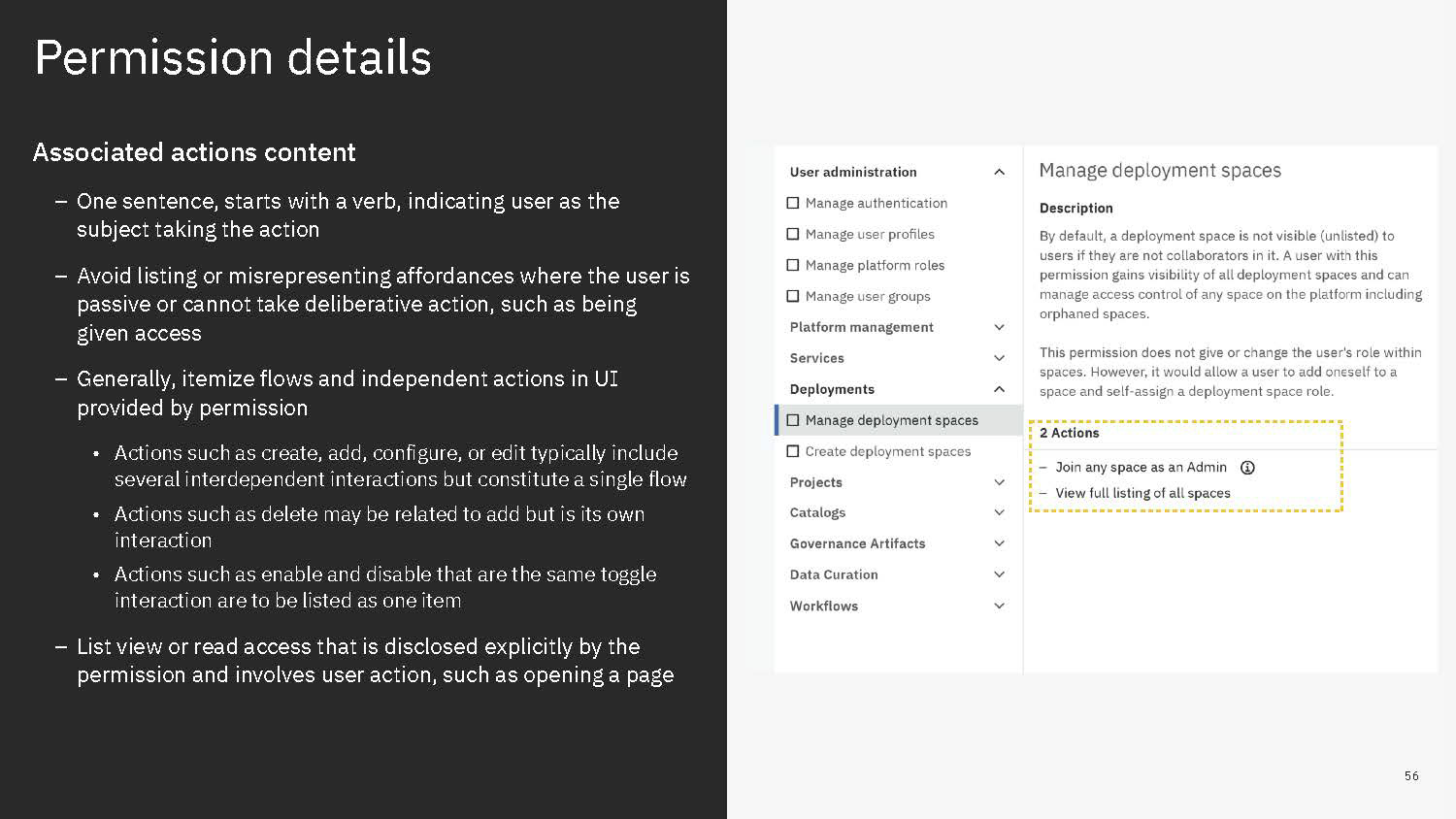
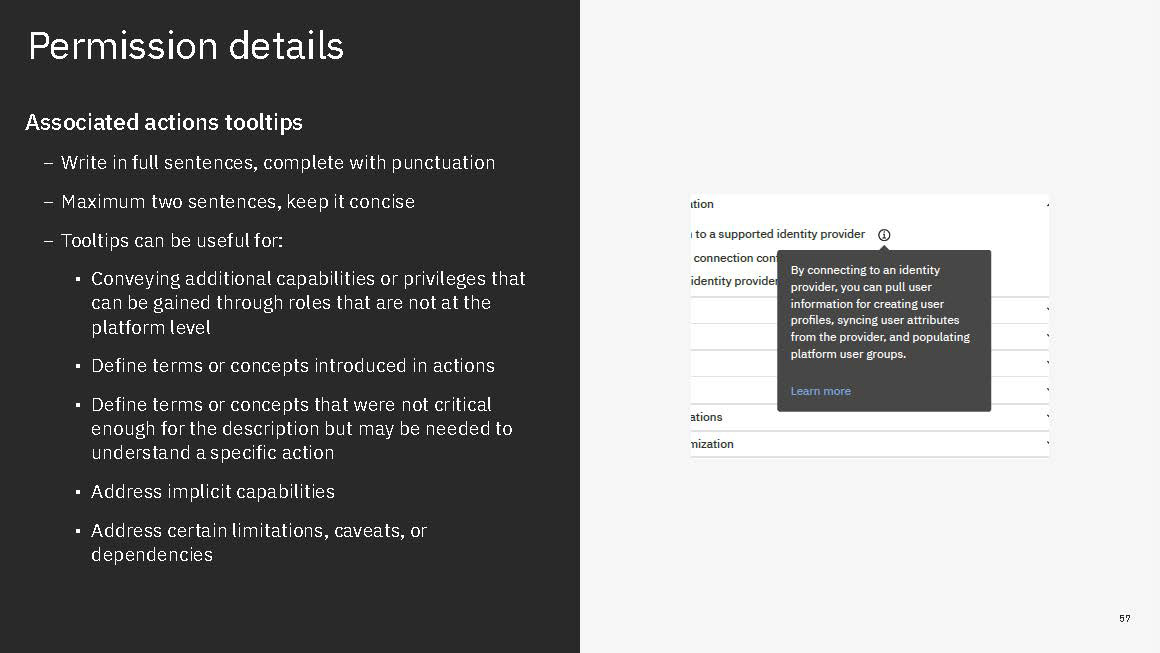
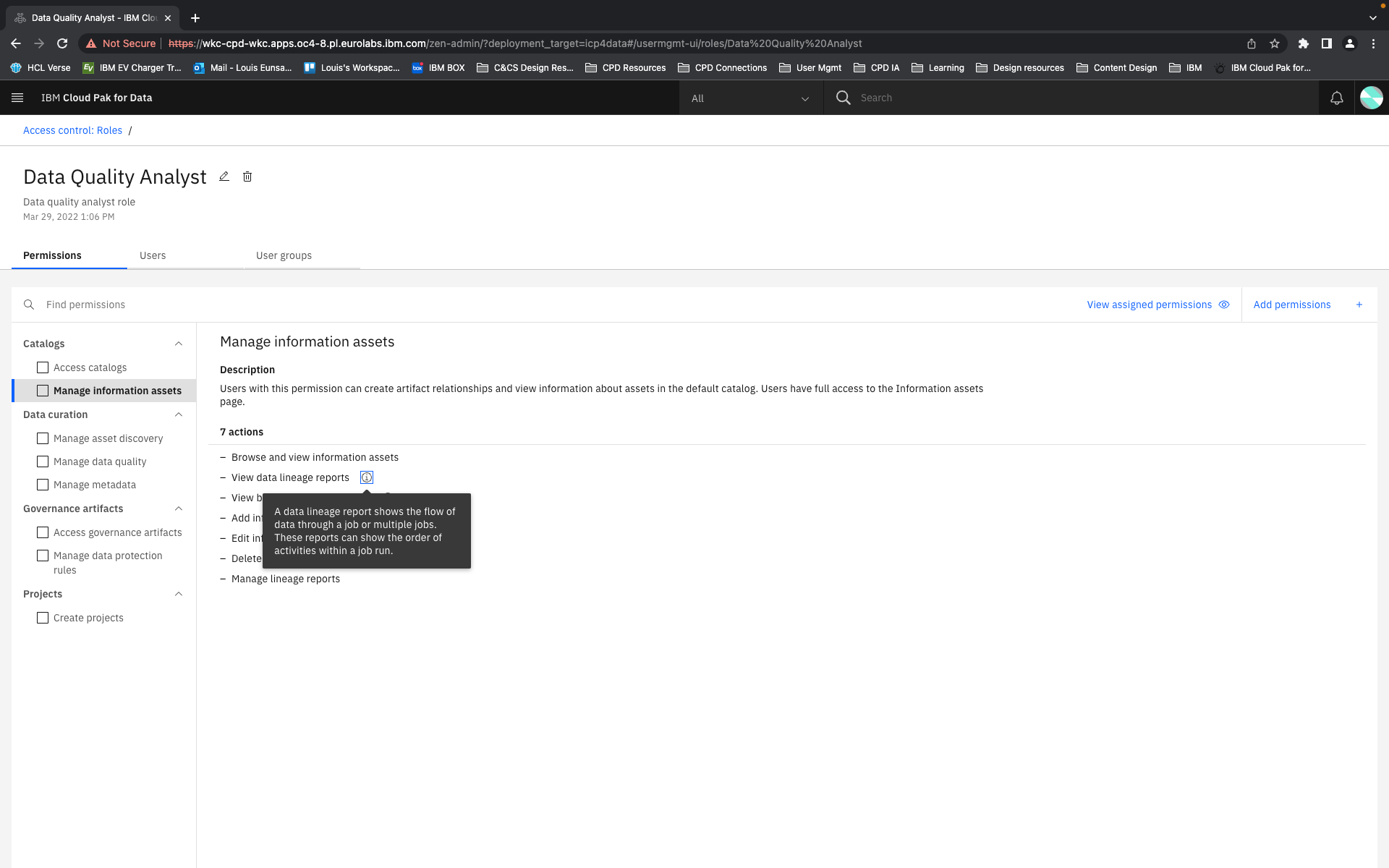
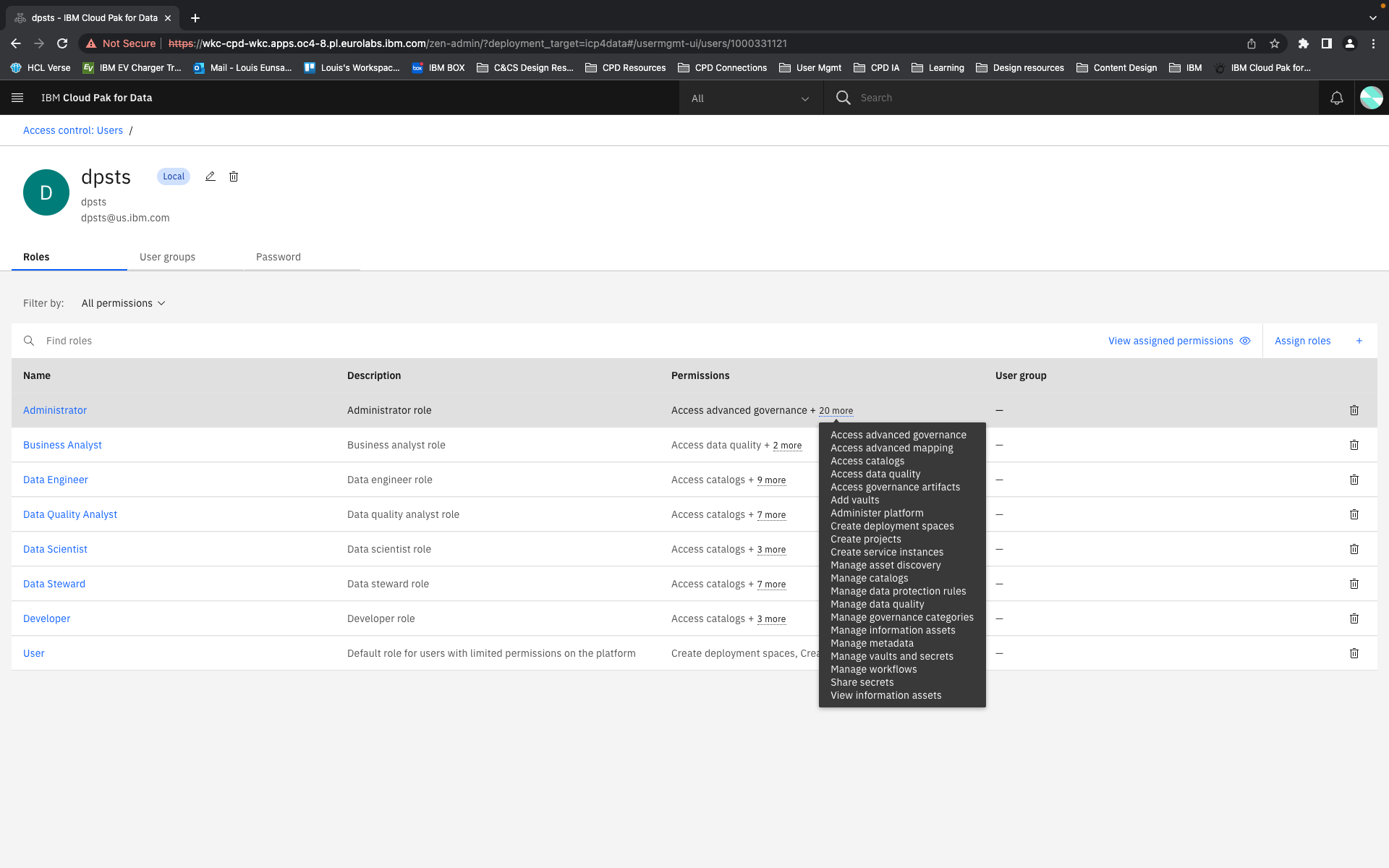
In our new structure, we introduced the concept of "actions". These are shown to users as the smallest units of privileges that compound into a bundled permission. Actions reflect the discrete capabilities that not only build up into a permission but also can be shared across permissions. They are more or less reflections of the permissions' actual composition but editorialized into easily read and understood terms.
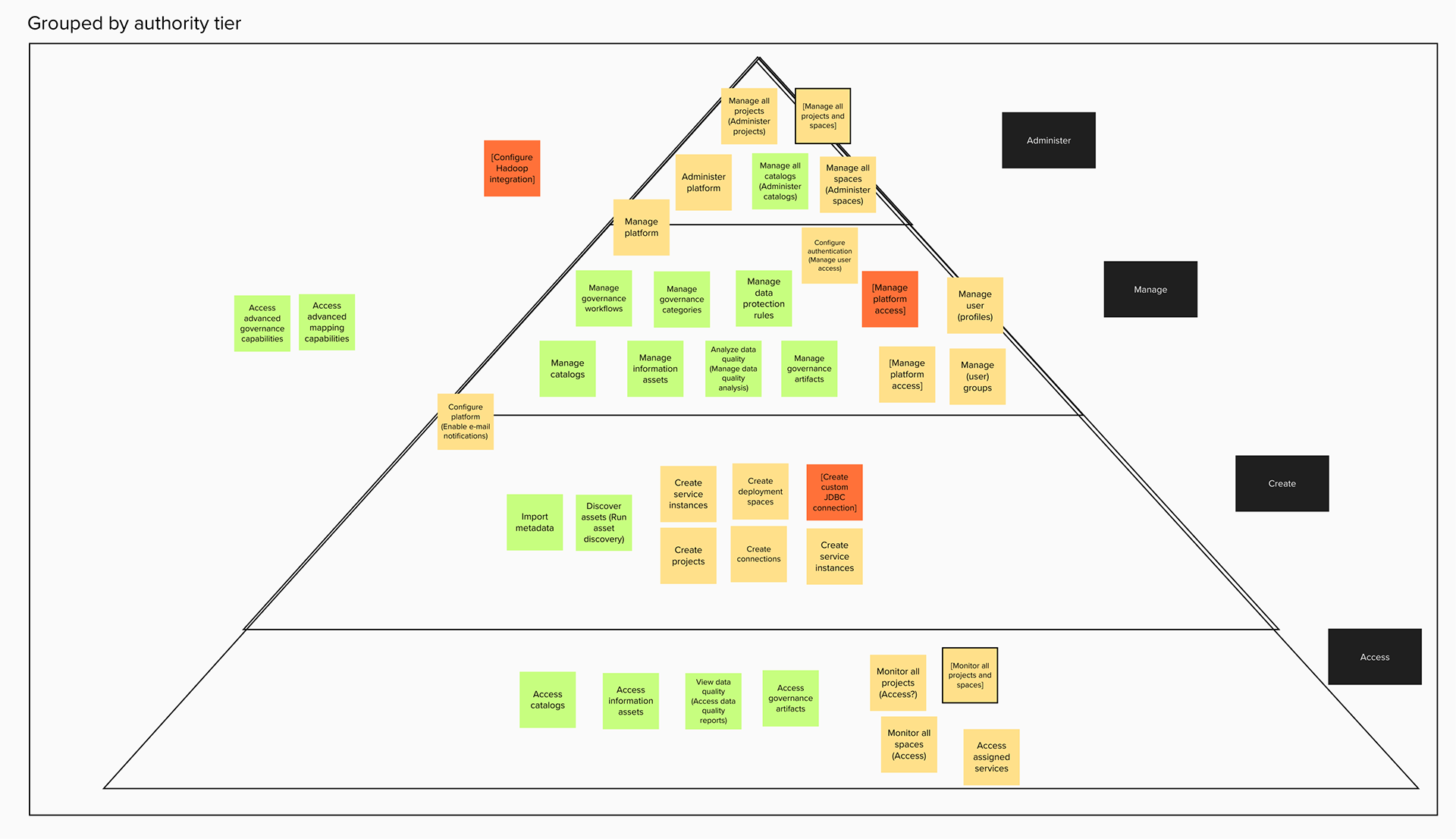
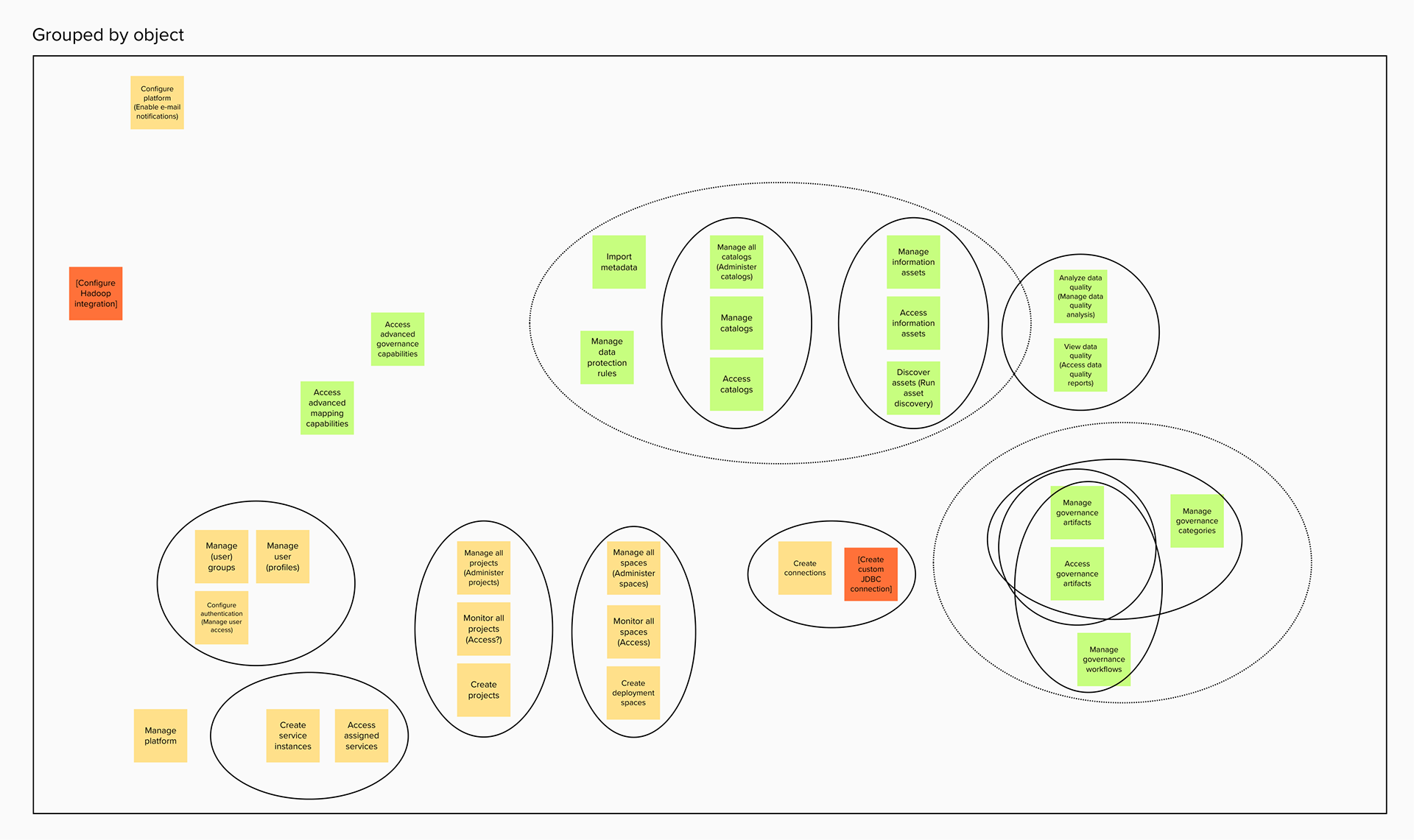
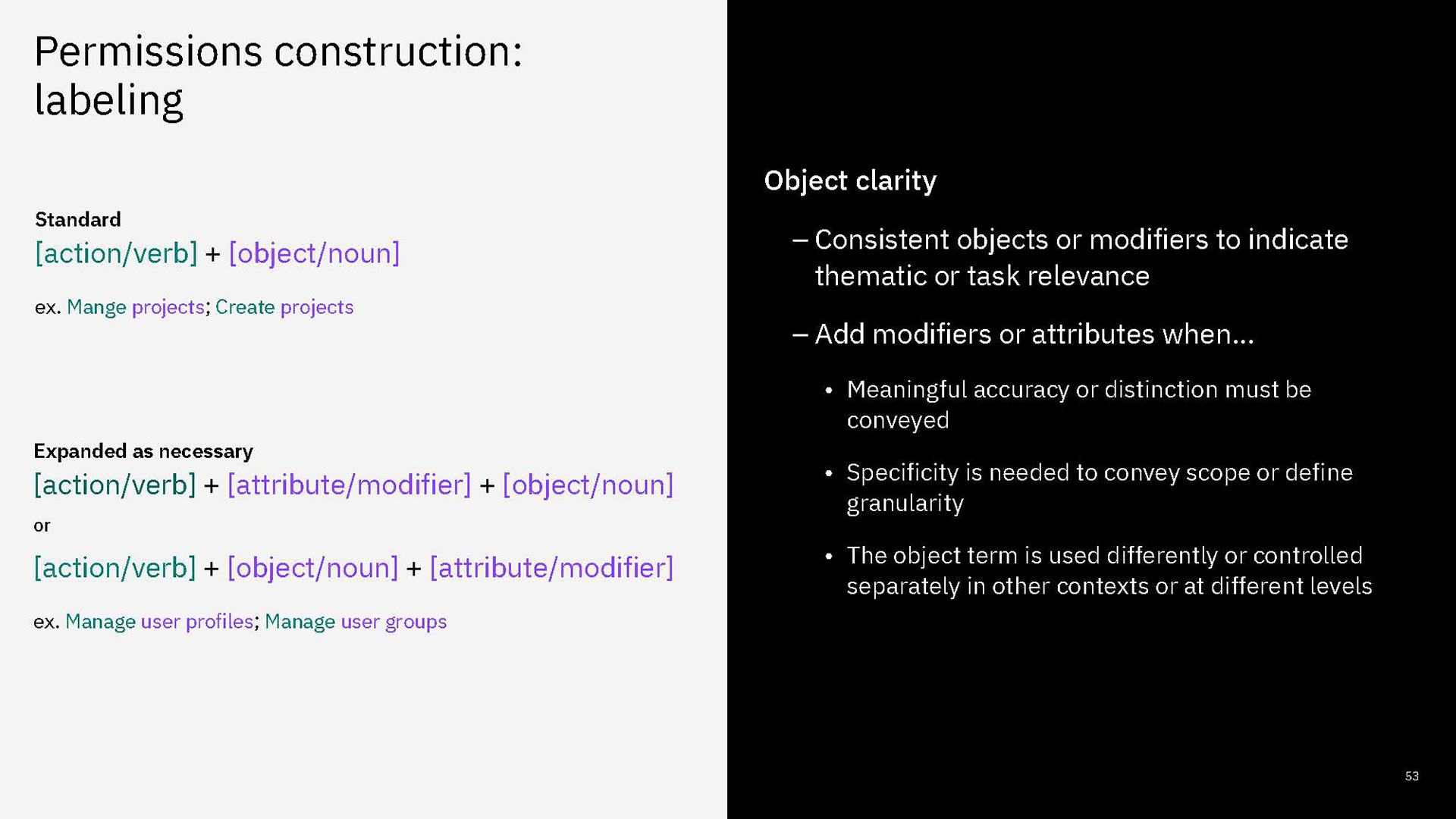
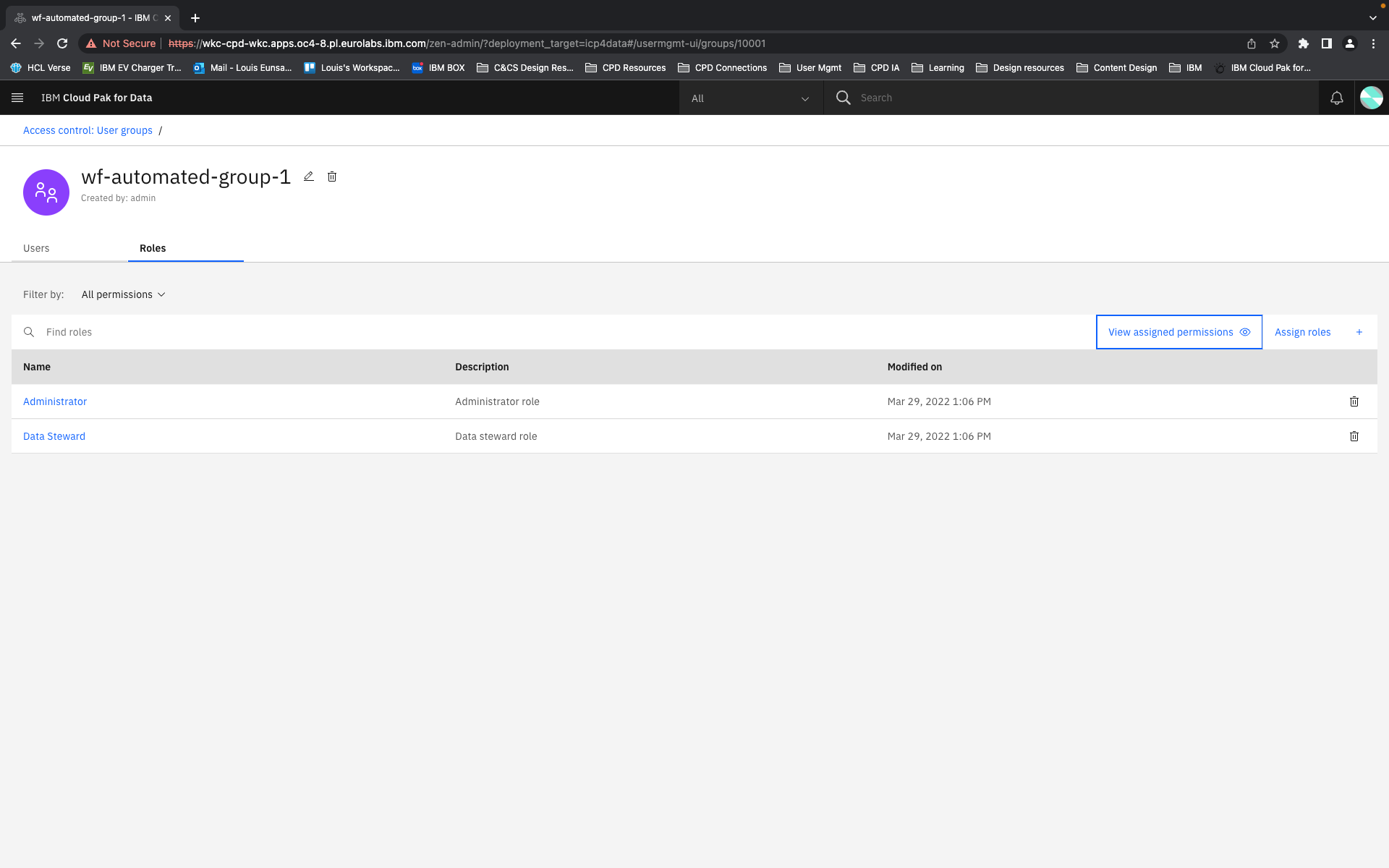
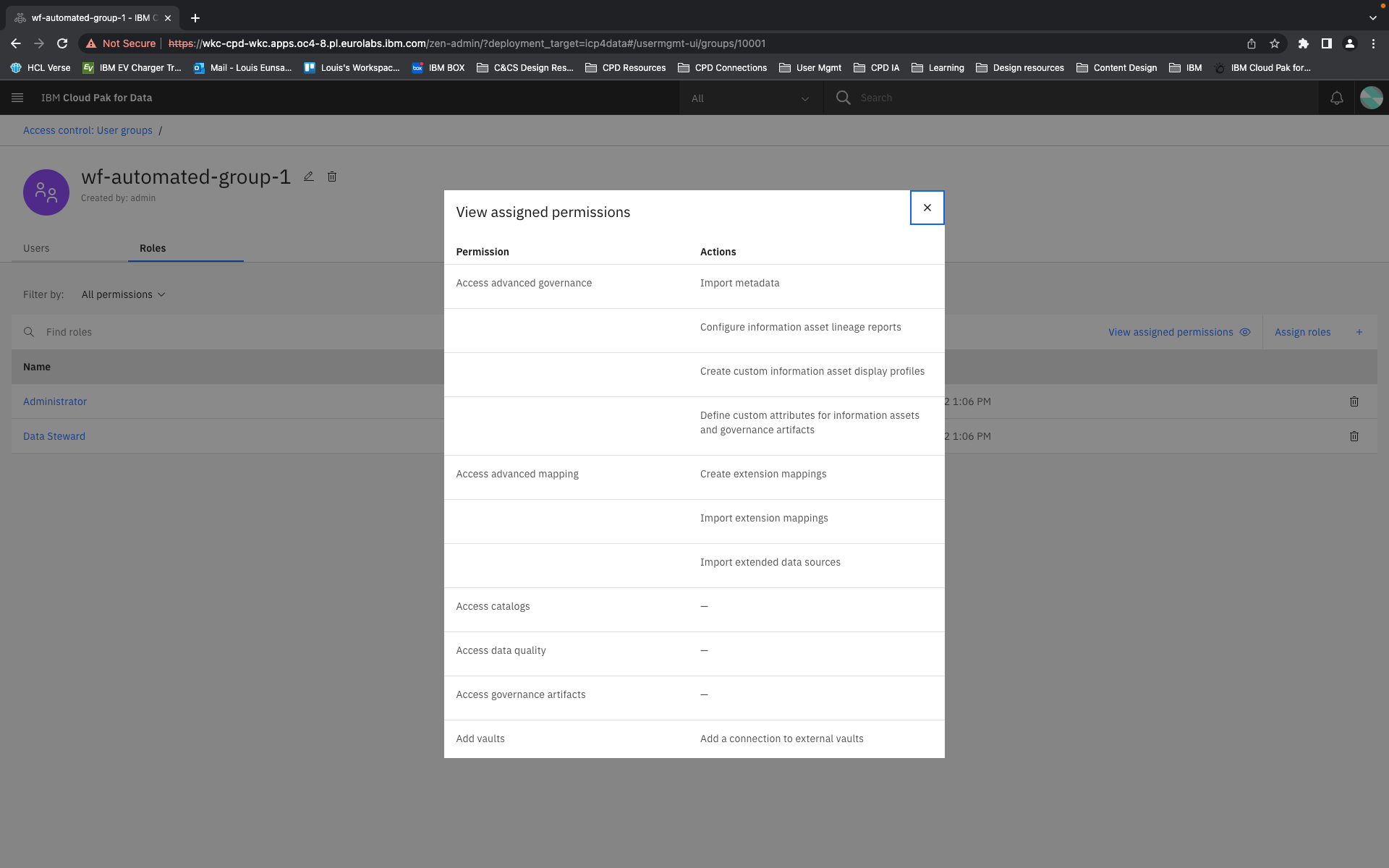
The conception of units of actions then allowed us to define that permissions as objects should be flat in their hierarchy, as they are in the back-end. That means, even if permissions concern similar objects and some have all the same privileges and authorities and some more, or a permission is a superset of the privileges of several other permissions, they are understood and presented as individual permissions. There is no longer any confusion as to whether getting one higher permission means inheriting the lower permissions as well or not. You can get multiple permissions that overlap in their actions but that just means your actions aggregate but you get every individual permission that your are explicitly assigned.
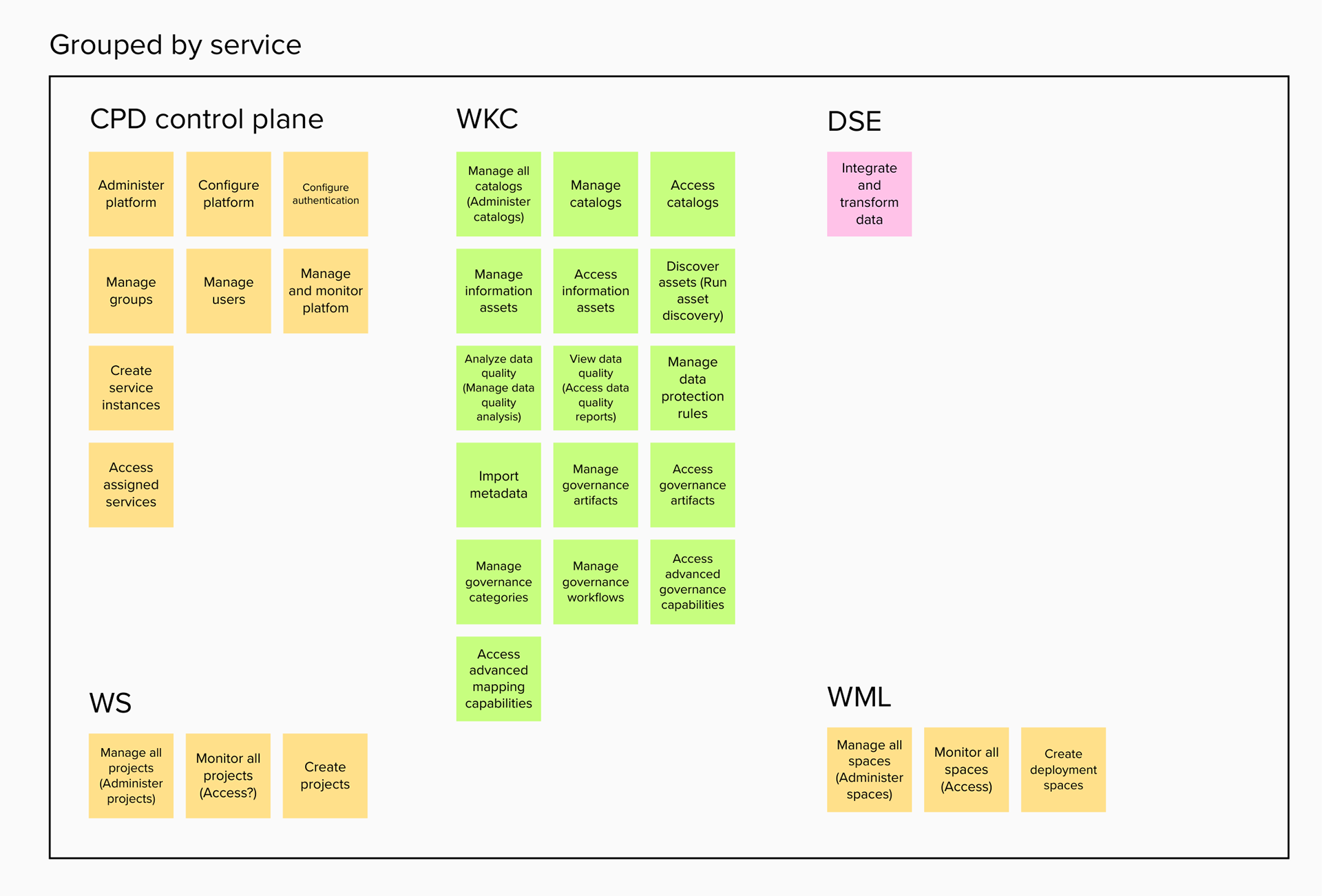
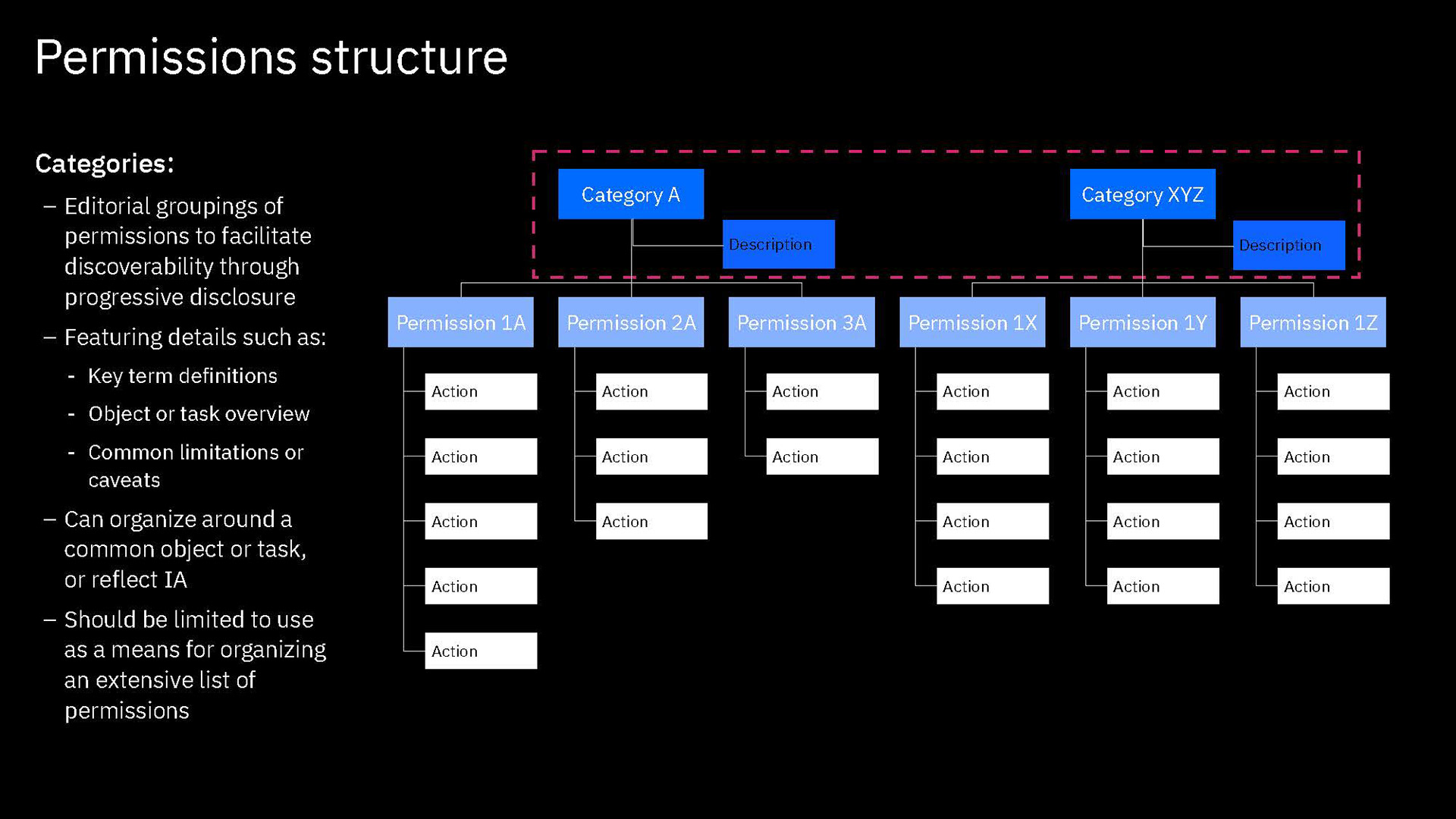
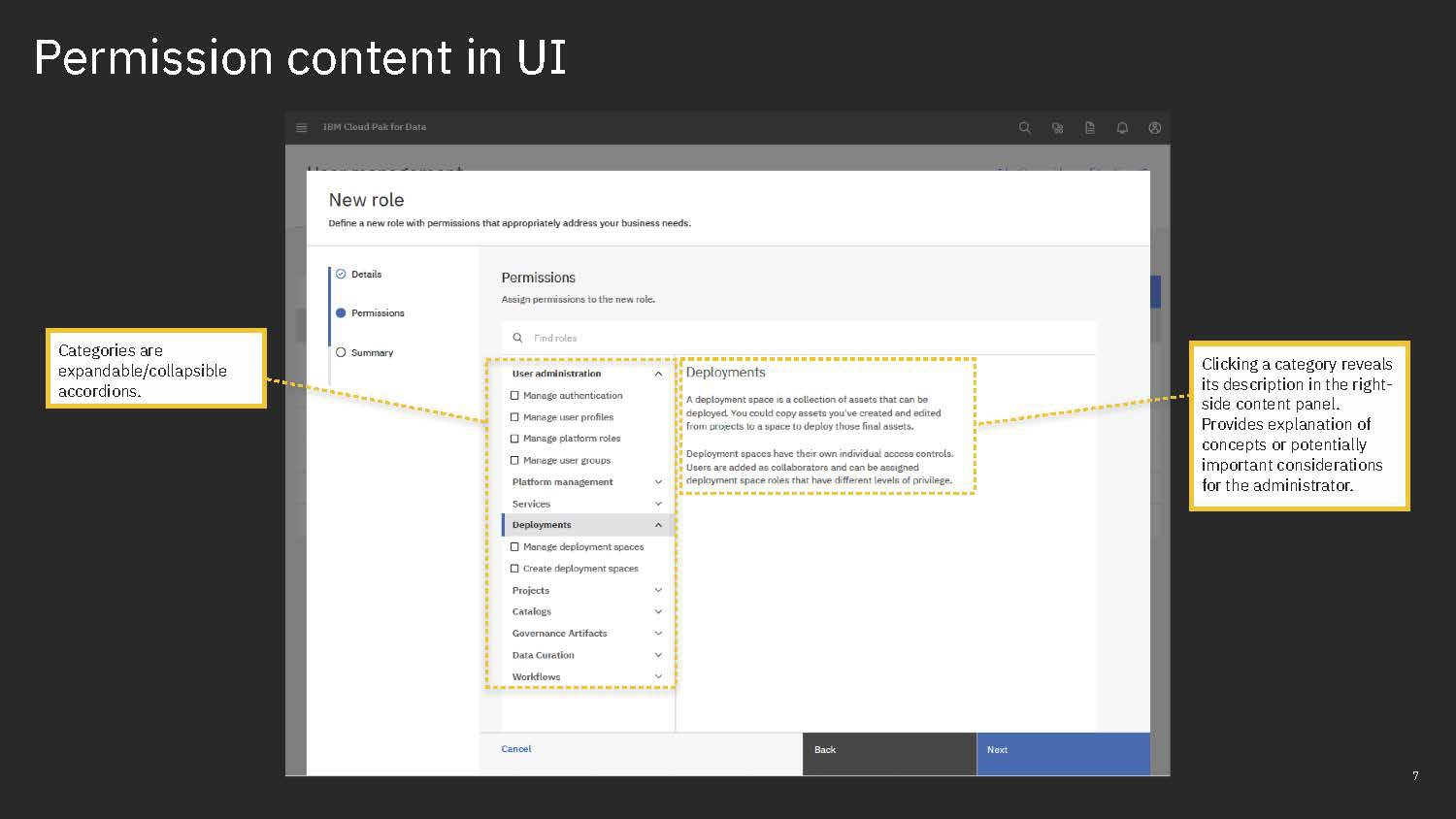
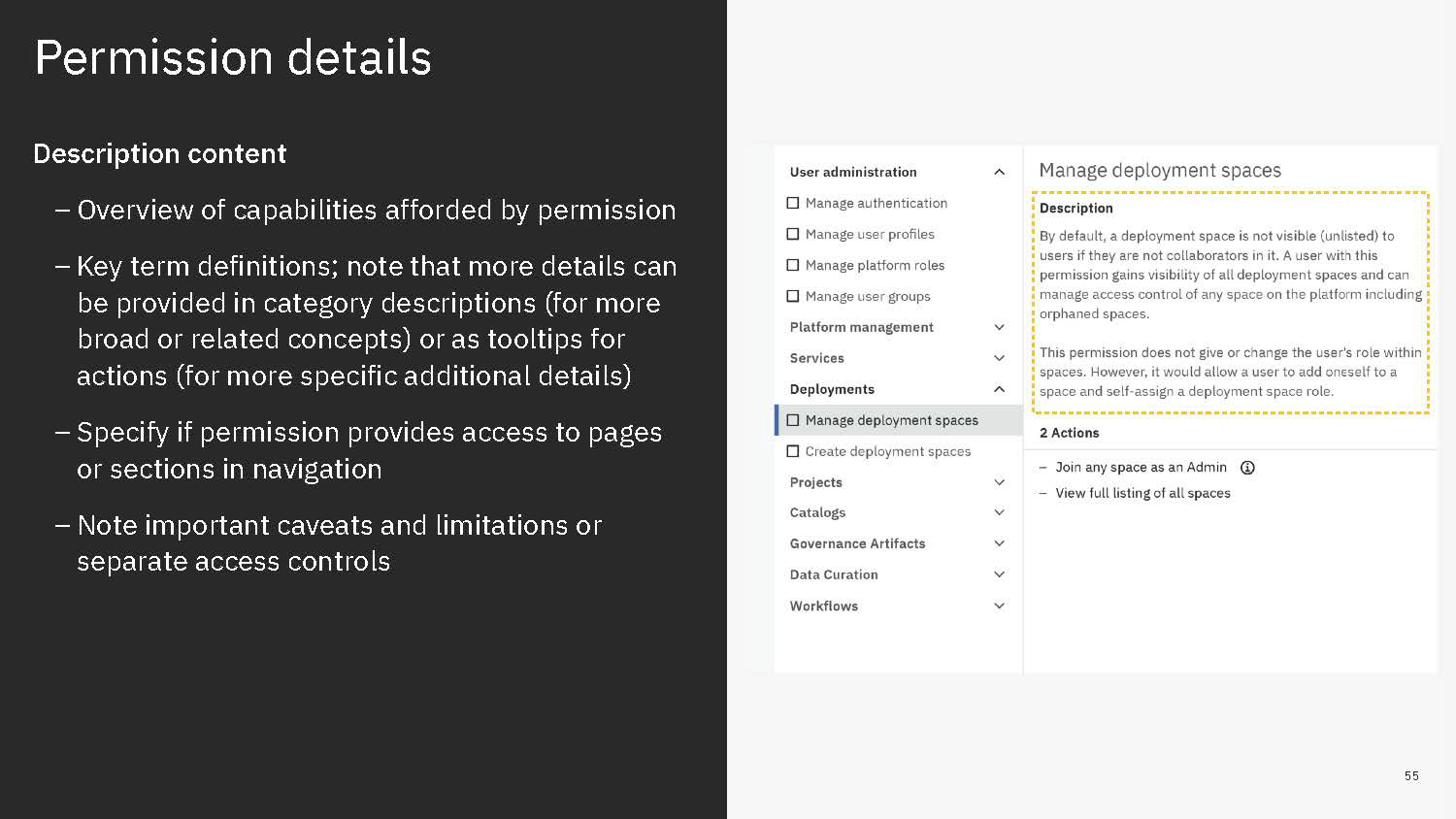
Permissions are then grouped together in categories. These categories are purely editorial and front-end content and organize permissions together by objects or by a task-theme. It allows permissions that affect common objects or domains to sit together to be found more quickly and compared more easily.
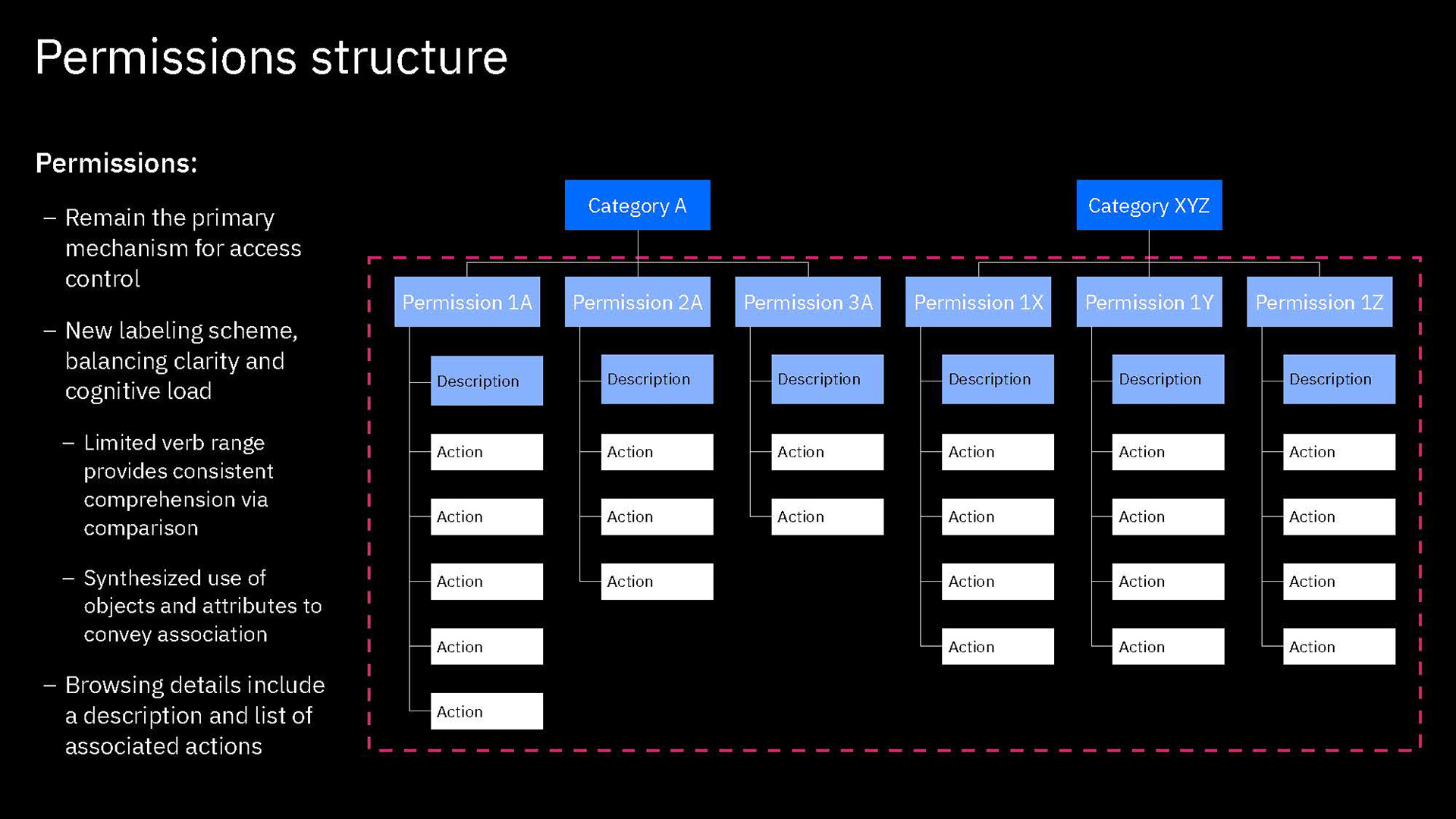
Content is mainly served at these three levels: actions, permission, and categories. Actions not only clearly list capabilities, but when some need more explanation, definitions, or have certain conditions, are appended with a tooltip to learn more. Permissions are not only a culmination of actions but also offer a description that lays out term definitions and other details about the permission that are not necessarily actions, such as authorizations that allow passive action to be taken on someone assigned a given permission. Categories not only group together permission but they also have descriptions that both offer definitions of terms but also a summary of common qualities to grouped permissions.
Moreover, sorting, filtering and searching mechanisms were thought of at each level. Some sorting would be built in: categories are a de-facto sort of permissions, permissions are sorted according to authority tier in each category, and categories are sorted alphanumerically. Search applies to category labels, permission labels, and actions. And filtering would apply by permission authority tier level and by the associate service.